Prettier Usernames in Sitecore When Using Azure AD or Other Identity Providers
Kamruz Jaman - Solution Architect
29 Oct 2025
The Identity Server has been around in Sitecore for many years now, and provides centralized authentication for the different roles such as CM, CD and other services. It also makes it much easier to integrate external identity providers (e.g., Azure AD, Okta, Auth0) for federated authentication.
One of the most common integrations for our customers is with Azure AD, and luckily there is a sample configuration available in the default installation of Sitecore that makes it very simple to enable and configure for your own tenant.
What’s wrong with default usernames?
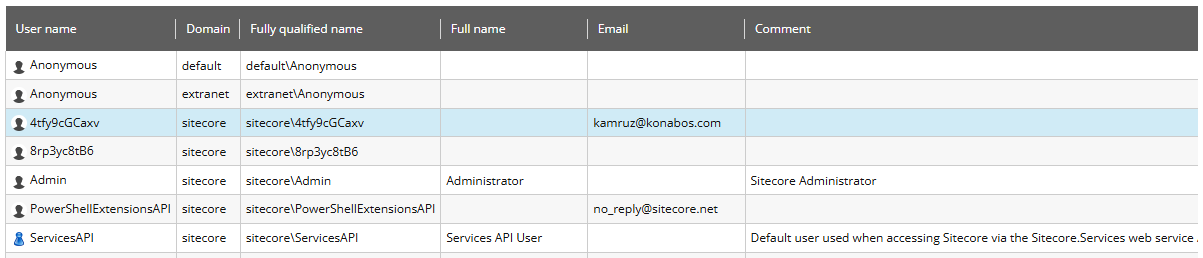
The problem with the default setup is that when the users created in your Sitecore instance, it generates a very random and unfriendly username which is just a random set of characters. This applies to integrations with all identity providers, not just Azure AD, so you would have the same issue with Okta and Auth0 for example.
The while it is fairly simple to find the actual user this random username is mapped to using the search functionality in the User Manager, this is an issue because:
- If a user has locked an item, it shows this random username
- Same when looking at item details, such as the user that created or last updated the item, or item version history or information within workflows
- All audit information in the logs also records this unfriendly username
- Not all users may not have access to the User Manager
- It's still a two-step process instead of it being immediately obvious who the user is
Generating friendly usernames
Thankfully there is an easy solution to make these usernames more meaningful and understandable.
Create a new class:
1using Microsoft.AspNet.Identity;
2using Microsoft.AspNet.Identity.Owin;
3using Sitecore.Owin.Authentication.Identity;
4using Sitecore.Owin.Authentication.Services;
5using Sitecore.SecurityModel.Cryptography;
6
7namespace Konabos.Authentication
8{
9 public class CustomUserBuilder : DefaultExternalUserBuilder
10 {
11 public CustomUserBuilder(ApplicationUserFactory applicationUserFactory, IHashEncryption hashEncryption) : base(applicationUserFactory, hashEncryption)
12 {
13 }
14
15 protected override string CreateUniqueUserName(UserManager<ApplicationUser> userManager, ExternalLoginInfo externalLoginInfo)
16 {
17
string hashDerivedName = base.CreateUniqueUserName(userManager, externalLoginInfo);
18
string domain = hashDerivedName.Substring(0, hashDerivedName.IndexOf('\\'));
19
var emailId = externalLoginInfo.ExternalIdentity.FindFirst("email")?.Value;
20
string providerKeyName = domain + @"\" + emailId;
21
// Check name not already assigned.
22
return userManager.FindByName(providerKeyName) == null ? providerKeyName : hashDerivedName;
23 }
24 }
25}Patch it in:
1<?xml version="1.0" encoding="utf-8" ?>
2<configuration xmlns:patch="http://www.sitecore.net/xmlconfig/" xmlns:set="http://www.sitecore.net/xmlconfig/set" xmlns:role="http://www.sitecore.net/xmlconfig/role">
3 <sitecore role:require="ContentManagement or Standalone">
4
5 <!-- add custom domain to list of valid domains -->
6 <domainManager set:defaultProvider="config">
7 <domains>
8 <domain id="konabos" type="Sitecore.Security.Domains.Domain, Sitecore.Kernel">
9 <param desc="name">$(id)</param>
10 <ensureAnonymousUser>false</ensureAnonymousUser>
11 </domain>
12 </domains>
13 </domainManager>
14
15 <federatedAuthentication>
16
17 <!-- set new users created from id server to be created in custom domain -->
18 <identityProviders>
19 <identityProvider id="SitecoreIdentityServer">
20 <domain>konabos</domain>
21 </identityProvider>
22 </identityProviders>
23
24 <!-- map user properties passed from id server to sitecore user -->
25 <propertyInitializer>
26 <maps>
27 <map name="set FullName" type="Sitecore.Owin.Authentication.Services.DefaultClaimToPropertyMapper, Sitecore.Owin.Authentication" resolve="true">
28
<data hint="raw:AddData">
29
<source name="name" />
30
<target name="FullName" />
31
</data>
32 </map>
33 <map name="set Email" type="Sitecore.Owin.Authentication.Services.DefaultClaimToPropertyMapper, Sitecore.Owin.Authentication" resolve="true">
34
<data hint="raw:AddData">
35
<source name="email" />
36
<target name="Email" />
37
</data>
38 </map>
39 </maps>
40 </propertyInitializer>
41
42 <!-- control how the username is generated rather than random value -->
43 <identityProvidersPerSites>
44 <mapEntry name ="all sites">
45 <externalUserBuilder set:type="Konabos.Authentication.CustomUserBuilder, Konabos.Authentication" />
46 </mapEntry>
47 </identityProvidersPerSites>
48
49 </federatedAuthentication>
50
51 </sitecore>
52</configuration>This will map across the full name and email address of the user from your Azure AD mapping.
Keeping things organized by using a custom domain
We are doing a couple of extra things here.
We're patching in a new domain and tell it to use the config-based domain manager (rather than adding it through the Domain Manager) and we'll then create all users in this domain to help keep cleaner separation (rather than use the default Sitecore domain). We're also telling the Identity Server to use this as the default, and we can then pick this up in our code and apply it to the pretty usernames we are generating.
A small fix with big usability gains
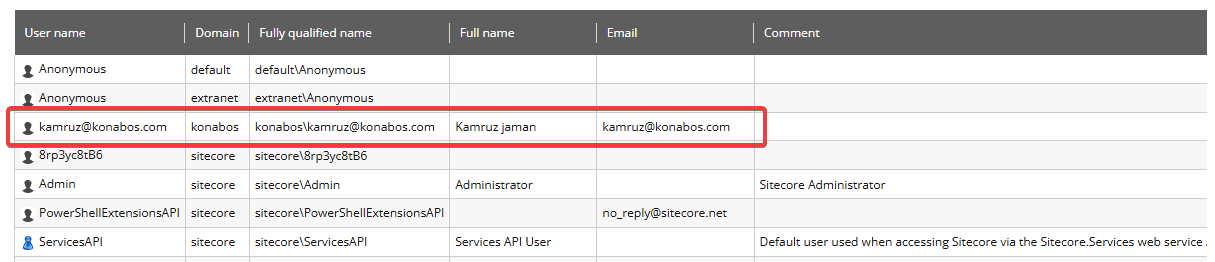
Now we have clean and easy to understand usernames, making it easier to understand who the user is. And since it's using the email address anyway, you can just email them directly if you need to speak with them
This small tweak improves auditability, user experience and sanity for content editors, and it’s one of those hidden gems that makes Sitecore administration smoother.

Kamruz Jaman
Kamruz is a 14-time Sitecore MVP who has worked with the Sitecore platform for more than a decade and has over 20 years of development and architecture experience using the Microsoft technology stack. Kamruz is heavily involved in the Sitecore Community and has spoken at various User Groups and Conferences. As one of the managing partners of Konabos Inc, Kamruz will work closely with clients to ensure projects are successfully delivered to a high standard.


Share on social media