Where to start building security guidelines at your company?
Lukasz Skowroński - Senior Solutions Architect
1 Mar 2024
Security is a hot topic nowadays. A growing number of companies using more and more advanced technologies and moving to the internet space also require more awareness of the risks and cyber security. You are lucky if you thought about cyber security before someone attacked you – some companies do not have so much luck and start building their security policies after the first loss of data or money. In this article, we will try to show you one of the available paths to start your journey.
Cybersecurity framework
When you do not know where to start it is usually good to find a framework that can help you to add some structure to everything that you are planning to do. A framework that is prepared by someone with larger expertise.
The National Institute of Standards and Technology (NIST) developed a framework called “Cybersecurity framework” (CSF) which is used by a variety of companies and governments. At the end of February 2024, NIST will release CSF 2.0 and we will use a draft of it to discuss what everyone can learn from it.
A framework by its nature helps:
- Define common language for understanding, managing and describing cybersecurity risks
- Identify and prioritize actions that they may take to reduce cybersecurity risk and manage any risks that remains
A common language can be worth learning if you plan to adjust to the standard and cooperate with other companies using the same standard. The same language may be useful also if you want everyone at your company to understand what is hidden behind the words that you are using (it also works the opposite way). In this article, we will focus though on identifying and prioritizing risks and actions.
It is also worth noting at this point that even if you read CSF documents you do not need to follow everything that is their letter for letter (unless you do not plan to pass the certificates) – you can use only these parts that are useful for you.
What you must know
Try to imagine that one day you must start building your plan to increase the security level at your company. Questions that must be answered will be almost always the same:
- What systems/infrastructure must be protected?
- How can we protect specific parts of the environment?
- How can we detect issues and possible attacks?
- What to do when something happens?
CSF consists of functions, categories, and subcategories that help to add structure to the given answers.
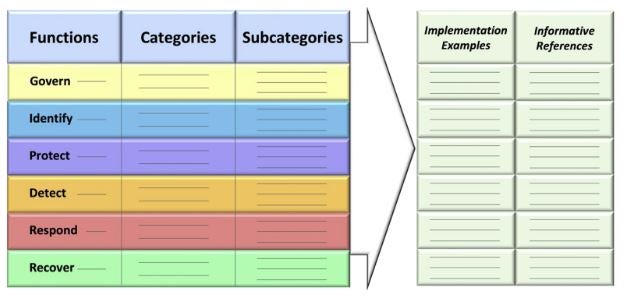
Fig 1. Cybersecurity Framework Core (NIST)
Functions “identify”, “protect”, “detect”, “respond” and “recover” perfectly fit to actions that you would think of when you build answers for the questions from the above paragraph. Starting from this point you may notice that thanks to CSF you will not forget to address important areas of your security. The only function that is not so obvious is “govern” – let’s focus on it for now.
The Govern function by CSF is defined as “Establish and monitor the organization’s cybersecurity risk management 192 strategy, expectations, and policy. The Govern Function is cross-cutting and provides outcomes to inform how an organization will achieve and prioritize the outcomes of the other five Functions in the context of its mission and stakeholder expectations.”
In simple words, we can define the governing function as the step that defines the plan we want to follow and as with any other plan, there must be time to review the state of work. If you think about it, continues improvement is something that can be presented only as circle, and this is how NIST sees it too:
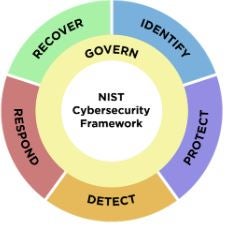
Fig 2. Framework functions
Starting from the Govern function through Identify, Protect, Detect, Respond, and Recover, we should be ready to repeat all actions in circles as security is not a state but a process.
Profiles
When you prepare your objectives and identify environments and expectations you will realize that there will be a need to divide all of what you find out into the related sets. To answer this need CSF defines profiles that have two states - current and target – and you can have multiple of those.
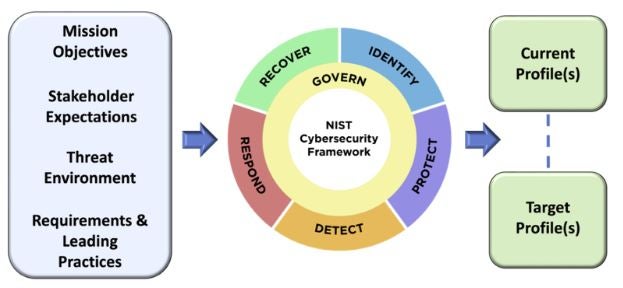
Fig 3. Cybersecurity Framework Profiles
A Current Profile covers the Core’s outcomes that an organization is currently achieving (or attempting to achieve) and characterizes how or to what extent each outcome is being achieved.
A Target Profile covers the desired outcomes that an organization has selected and prioritized for achieving its cybersecurity risk management objectives.
With the creation of the profiles, we are moving forward in the details of security improvements.
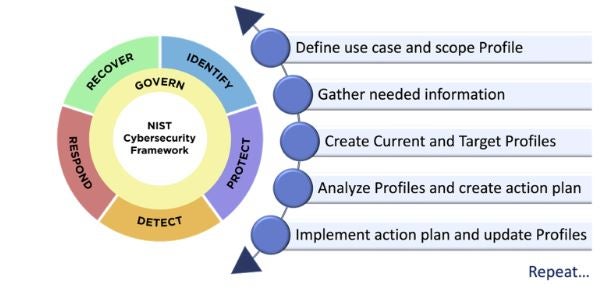
Fig 4. Steps for creating and using CSF profiles
To define profiles fully in compliance with CSF we would need to make this article at least few pages longer. You can check some of the examples here: https://www.nist.gov/cyberframework/examples-framework-profiles.
If compliance is not your goal and you simply want to start dealing with your security, you can try to think about your profiles in the following way.
- Current profile -> Target profile
- Not secured network -> Secured network
- Risky data management -> Secured data management
These examples do not comply with the standard but allow us to start quickly and then adjust to the standard (if needed) during one of the future iterations.
Summary
Within this article, we covered only the first part of the NIST’s cybersecurity framework. There is a lot more to cover that would help you to make the plan more gradual and precise. There are defined tiers that let you set the priorities. There are listed categories and subcategories that you can use as a cheat sheet as it contains over a hundred points worth of consideration during planning the security strategy. Visit NIST’s website for more information.
We hope that with this introduction to CSF we helped you to start building the cyber security of your company and we made you curious enough to dive deep into the topic soon.
Dive deeper into the NIST cybersecurity framework with our expert guidance. Gain insights into the defined tiers, categories, and subcategories that shape a robust security plan. Let us help you navigate the complexities and set priorities effectively. Tell us about your project and schedule a call with us today.

Lukasz Skowroński
For over 18 years, I have developed numerous solutions for customers worldwide. I specialize in DXP platforms, including Sitecore, Xperience by Kentico, and various CMSs such as Umbraco. So far, I have been awarded nine times with the Sitecore MVP title, once with the Kentico MVP. I continuously support various communities by organizing local user groups and larger conferences like Sitecore User Group Conference Europe (SUGCON Europe), as well as by sharing knowledge through blog posts.



Share on social media